Single Sign-On (SSO) User Authentication in Prokeep
What is Single Sign-On (SSO)?
Single Sign-On (SSO) allows users to access multiple applications with a single set of login credentials. It simplifies the login process, enhances security, and improves user experience. For administrators, SSO streamlines user management, reduces password-related issues, and provides centralized control over access permissions.
Who Can Get SSO with Prokeep?
SSO setup requires collaboration between Prokeep and your IT administrator and depending on your account level may require an upgrade or a small fee. Please contact your Prokeep Customer Success Manager to determine if Prokeep SSO is right for your organization.
Common Terms in SSO:
- Identity Provider (IdP): Manages user authentication and provides user information to Service Providers. The credentials used to sign in with are the IdP credentials.
- Service Provider (SP): The application or system that users want to access, such as Prokeep.
- SAML 2.0: Security Assertion Markup Language 2.0 is an XML-based protocol for authentication and authorization.
Example of SSO with Prokeep:
Imagine a scenario where a company implements SSO with Prokeep using Microsoft Entra as the Identity Provider (IDP). Here's how the login flow would work and the benefits it offers:
Scenario: User Accessing Prokeep:
- The user goes to their Prokeep sub-domain (e.g., sub-domain.prokeep.com).
- If already logged into Entra, they can directly access Prokeep without entering additional credentials.
- If not logged in, they're redirected to the Entra login page.
- They enter their Entra credentials (username and password).
- Entra verifies the credentials and sends an authentication response to Prokeep.
- Prokeep verifies the response and grants access to the user.
- The user is now logged into Prokeep without needing a separate Prokeep login.
Types of SSO Supported by Prokeep:
Prokeep specializes in Single Sign-On (SSO) using SAML 2.0 and supports a wide range of Identity Providers (IDPs) including Microsoft Entra, Microsoft Azure, Okta, JumpCloud, Google Workplace, and any SAML 2.0 compliant IDP.
- Basic SSO Authentication: This type of SSO allows users to log in to Prokeep using their existing credentials, typically in the form of an email address. It simplifies the login process and enhances security by reducing password fatigue.
- Just-In-Time (JIT) Provisioning: In addition to basic SSO authentication, Prokeep also supports Just-In-Time (JIT) provisioning. JIT provisioning automatically creates user accounts and assigns appropriate roles and permissions based on SAML attributes passed during the login process. This feature streamlines user management and ensures that users have the right access levels from the start. Explore detailed information about Prokeep's JIT User Provisioning feature here.
Setting Up SSO with Prokeep:
- Fill in the SSO Survey: Begin by filling out the SSO Survey [here] with details about your Identity Provider, previous SSO experience, and test account availability.
- Schedule a Call: Your Customer Success Manager (CSM) and Technical Account Manager (TAM) will reach out to schedule a call. During this call, the technical teams from both sides will coordinate to set up the SSO integration.
- Exchange Metadata and Information: During the call, exchange metadata and other necessary information to create a Custom SAML app on your Identity Provider's side.
- Load users into Prokeep: For Basic SSO, users need to be manually added to Prokeep before their initial login. If you prefer automatic user creation, we can set up JIT SSO (Just-In-Time Provisioning).
- Initial Configuration: Enter Prokeep's SSO details into your Identity Provider (IdP) and configure SAML settings. This includes the Prokeep Metadata URL, App ID, and Response URL.
- Testing: Conduct a test login to ensure SSO functionality for both Prokeep's browser-based app and mobile app.
- Finalization: Update the account bridge page and confirm SSO setup. Coordinate with Prokeep or your IT admin for live setup assistance.
Basic SSO Flow Chart:
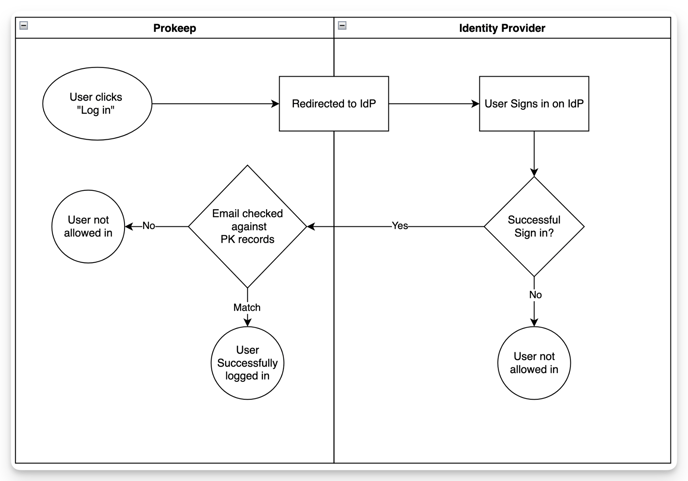
Additional Information:
- Supported Attributes: For Basic SSO, Prokeep requires a username in the format of an email address. For JIT provisioning, ensure that SAML attributes are passed for roles (admin, manager, member) and groups (locations).
- Basic SSO User Loading: Basic SSO requires that users are manually added to Prokeep before their initial login. To authenticate successfully, users must have a representation in Prokeep in the form of a user account with an email address.
- Browser and Mobile Support: SSO authentication is supported for both Prokeep's browser-based application and mobile application, providing a seamless user experience across platforms.
- Multiple Factor Authentication (MFA): Prokeep supports multiple-factor authentication through SSO, adding an extra layer of security to user logins.
- Security Practices: When SSO is in place, Prokeep uses the credentials from the Identity Provider (IdP) for authentication and does not store username/password information. Customers can enhance security further by setting up Multi-Factor Authentication (MFA) and implementing additional security measures like geofencing and password requirements.
- Single Sign-Off (SSO) Support: Please note that Prokeep does not currently support Single Sign-Off (SSO). Users will need to log out separately from Prokeep and their Identity Provider (IdP) if logged in via SSO.
- Dual-Login Options: Users can log in via their designated sub-domain (e.g., sub-domain.prokeep.com), which redirects them to their Identity Provider (IdP) for authentication before accessing Prokeep as the Service Provider (SP). Alternatively, users can directly log in via their IdP for quick and convenient access.
